Understanding IT Risk Assessment: A Comprehensive Guide by Timspark Experts
Understanding IT Risk Assessment: A Comprehensive Guide by Timspark Experts
Last updated:
At Timspark, we’ve seen firsthand how a single overlooked vulnerability can snowball into a full-scale crisis—whether it’s a stealthy phishing attack slipping past defenses or a critical system going dark during a natural disaster. That’s why we believe a solid IT risk assessment isn’t just a regulatory checkbox—it’s your organization’s digital safety net.
Imagine this: your team is about to launch a new platform, everything is polished and ready—until an unexpected malware outbreak delays the rollout, exposing sensitive customer data and putting your brand at risk. What if you had foreseen the weak point weeks earlier? That’s the power of an effective risk assessment—spotting cracks before they break the foundation.
An IT risk assessment is a structured process for identifying, analyzing, and evaluating risks to your information systems, as outlined in NIST Special Publication 800-30r1. At Timspark, we help organizations uncover hidden risks—such as outdated software patches or misconfigured access controls—and analyze how these could impact their daily operations, finances, and reputation.
Whether you’re shielding data from cyberattacks or preparing for unpredictable disruptions, a robust risk assessment process empowers you to make smarter, faster decisions. It prioritizes what matters most, aligns your security strategy with your business goals, and helps ensure your organization can weather any storm.
In this guide, we’ll walk you through the essentials of IT risk assessment—from understanding its purpose to identifying top data security threats for 2025. Our goal? To help you strengthen your cybersecurity posture, meet evolving compliance requirements, and stay one step ahead in an increasingly complex digital world.
Why IT risk assessments matter
Every day, organizations trust their systems to handle everything from payroll processing to customer interactions and mission-critical logistics. However, lurking behind every login and data transfer is a potential threat—malware, insider errors, ransomware, or even environmental hazards such as fires or floods.
At Timspark, we’ve helped clients recover from unexpected breaches that started small—an unmonitored endpoint or an expired SSL certificate—and escalated into major service outages. The lesson is always the same: you can’t secure what you don’t understand.
That’s where risk assessments come in. They reveal the full threat landscape specific to your systems, helping you:
- Pinpoint potential threats and vulnerabilities hiding in plain sight.
- Evaluate the likelihood and impact of worst-case scenarios.
- Prioritize risks based on urgency and business impact.
- Make strategic, data-driven decisions for mitigation and response.
Regular risk assessments don’t just help you avoid costly mistakes—they support compliance with frameworks and regulations and give your team a clear, actionable roadmap for cyber resilience. In today’s hyper-connected environment, being reactive is no longer enough. Proactive, strategic risk assessments are how smart organizations maintain their security.
Who needs an IT risk assessment?
Short answer: everyone who depends on technology to operate.
From fast-growing startups to government agencies and global enterprises, every organization stands to gain from understanding its risk exposure. At Timspark, we take a holistic view—applying risk assessments not only to systems, but also to the people, processes, and goals they support.
Our experts guide assessments across three critical dimensions:
- Organizational Strategy: Aligning cybersecurity efforts with business priorities.
- Business Operations: Safeguarding the processes that keep your organization running.
- Information Systems: Securing infrastructure, data, and digital assets down to the code.
Whether you’re a CIO seeking strategic insight or an IT security lead identifying system-level threats, risk assessment results provide the clarity you need to act with confidence.
How to conduct an IT risk assessment
In today’s hyperconnected world, conducting an IT risk assessment isn’t just a checkbox—it’s a mission-critical practice. At Timspark, we’ve seen firsthand how organizations can either thrive or fall depending on how well they anticipate, evaluate, and mitigate risks.
Whether you’re dealing with an aggressive ransomware outbreak or a silent system misconfiguration, a well-structured approach helps you stay proactive. Here’s how we guide our partners through a thorough IT risk assessment that truly protects what matters most.
Step 1: Prepare for the risk assessment
Every successful journey begins with a clear map. We always start by aligning the risk assessment with the organization’s core mission. What systems are vital? What data must be safeguarded? Who are the key players?
At Timspark, we gather stakeholders—from tech leads to compliance officers—to bring everyone into the same room (physically or virtually). We’ve helped teams struggling with siloed risk ownership transform into a unified force. This early alignment ensures that the assessment is relevant, focused, and tailored to business objectives.
Step 2: Identify threats and vulnerabilities
Threats don’t always knock on the front door. Some slip in through legacy software, overlooked configurations, or unsuspecting employees.
We recall a case where a retail company underestimated its exposure through an old vendor portal. The vulnerability was minor—until it wasn’t. A targeted phishing campaign leveraged it, causing weeks of disruption.
That’s why we emphasize identifying both adversarial threats (like cyberattacks or insider sabotage) and non-adversarial risks (like server outages or natural disasters). Using a combination of automated tools, expert review, and real-world threat intelligence, we help organizations develop a comprehensive and actionable threat model.
Step 3: Assess likelihood and impact
Here’s where strategy meets reality. At this stage, we help quantify the likelihood of a threat and its potentially devastating impact.
For instance, a fintech startup we worked with faced a moderate likelihood of a brute-force attack, but the impact of compromised client credentials would be catastrophic. Together, we mapped out the potential fallout from each risk scenario to inform smarter prioritization and allocation of resources.
Whether qualitative or data-driven, the key is clarity. When you understand your risk landscape in terms of real-world consequences, decision-making becomes faster and more effective.
Step 4: Determine risk levels
Not all risks are created equal. Some demand immediate action; others are tolerable within the broader business context.
We employ clear prioritization methods—such as risk matrices, heat maps, or numerical scoring—to separate the signal from the noise. For example, a logistics company we supported discovered dozens of low-level vulnerabilities. But it was a single, high-risk API endpoint that posed the biggest threat. By zeroing in on what mattered most, we helped them deploy defenses where they counted.
Step 5: Develop mitigation strategies
This is where the rubber meets the road. Once we’ve identified high-priority risks, we collaborate with teams to formulate a tailored risk response strategy.
One of our partners in the health tech space faced challenges with legacy authentication systems. Rather than accepting the risk or patching it blindly, we helped them roll out multi-factor authentication across their infrastructure, minimizing disruption and maximizing protection.
Whether mitigating, avoiding, transferring, or accepting risk, what matters is documenting the plan and ensuring clear accountability.
Step 6: Communicate and monitor
The final step? Make it a habit, not a one-off exercise.
At Timspark, we build feedback loops into every engagement. We encourage our clients to treat risk assessments as living documents—updated as technology evolves, new tools are introduced, or after major incidents.
When a large media firm we worked with deployed a new cloud platform, our continuous monitoring approach detected a misconfigured access control within days, before any damage occurred. Early action made all the difference.
Key components of an effective IT risk assessment
Beyond the process itself, certain foundational elements define a successful IT risk assessment. These components form the DNA of a resilient cybersecurity strategy—one that grows stronger over time.
Stakeholder Involvement
We’ve seen it time and time again: the most successful risk assessments are driven by collaboration.
When Timspark facilitates an assessment, we ensure voices from across the organization are heard. Your IT team may flag outdated SSL protocols, while compliance officers stress GDPR alignment. Meanwhile, business leaders help identify which services are truly mission-critical.
Take our client in the transportation sector—they were so focused on operational uptime that they overlooked a hidden dependency in their invoicing platform. By including finance stakeholders, we identified and mitigated a critical risk that would have otherwise been overlooked.
Comprehensive threat and vulnerability identification
We utilize AI-driven tools, real-time threat feeds, and manual validation to identify blind spots that others might overlook.
For example, during a routine evaluation, we discovered a client’s S3 buckets were publicly accessible. The fix? Quick. But the discovery? Potentially game-saving.
Whether it’s outdated plugins, untrained staff, or third-party tools, we help uncover it all, ensuring that the organization has a 360-degree view of its risk exposure.
Risk prioritization
What should you fix first?
Our approach blends logic with insight. We help teams not only rank risks, but also understand why they matter. From minor inconveniences to existential threats, each is evaluated for likelihood and impact.
One client, an e-commerce giant, faced both a high volume of minor issues and a significant DDoS risk. We focused efforts on fortifying infrastructure against service disruptions, just in time for a seasonal sales spike.
Evaluation of existing controls
Having controls isn’t enough. They need to work.
Timspark conducts control evaluations that test the real-world effectiveness of your defenses. Are your firewalls configured correctly? Is MFA actually reducing account takeovers? Are employees passing phishing simulations?
When a SaaS firm brought us in, they had endpoint detection software installed, but it was silently failing. Our evaluation uncovered the lapse, which led to a comprehensive overhaul of endpoint security.
Documentation in a risk register
We don’t believe in assessments that live in PDFs and gather digital dust. A central, dynamic risk register turns insights into actions.
We create custom, accessible documentation for each partner, outlining the risk, identifying the owner, detailing existing controls, and specifying the next steps.
This clarity supports accountability, enables audits, and ensures that nothing falls through the cracks.
Ready to scale your team with top-tier IT talent?
Continuous monitoring and updates
Cybersecurity doesn’t stop. Neither should your assessments.
Timspark helps organizations move toward a continuous risk management model, leveraging automated alerts, real-time dashboards, and AI-driven threat detection.
A few months after a cloud migration, one of our clients noticed unusual API activity. Thanks to our monitoring setup, the threat was identified and mitigated before it could cause a breach.
Benefits of conducting regular IT risk assessments
In a world where cyber threats evolve faster than the technology that combats them, regular IT risk assessments have become mission-critical, not optional. At Timspark, we’ve seen firsthand how organizations that treat assessments as a strategic investment, rather than a compliance checkbox, gain a competitive edge.
We work with companies across industries—fintech, healthcare, logistics, SaaS—to help them build resilient systems, prevent cyber disruptions, and meet regulatory demands in a digital landscape that’s anything but predictable. Below, our experts guide you through the seven core benefits of conducting regular risk assessments, enriched with real-world examples, AI-powered tools, and performance metrics to inform your cybersecurity strategy for 2025 and beyond.
1. Enhanced cybersecurity posture
When cyber threats lurk behind every endpoint, proactive identification of risks becomes the cornerstone of digital resilience.
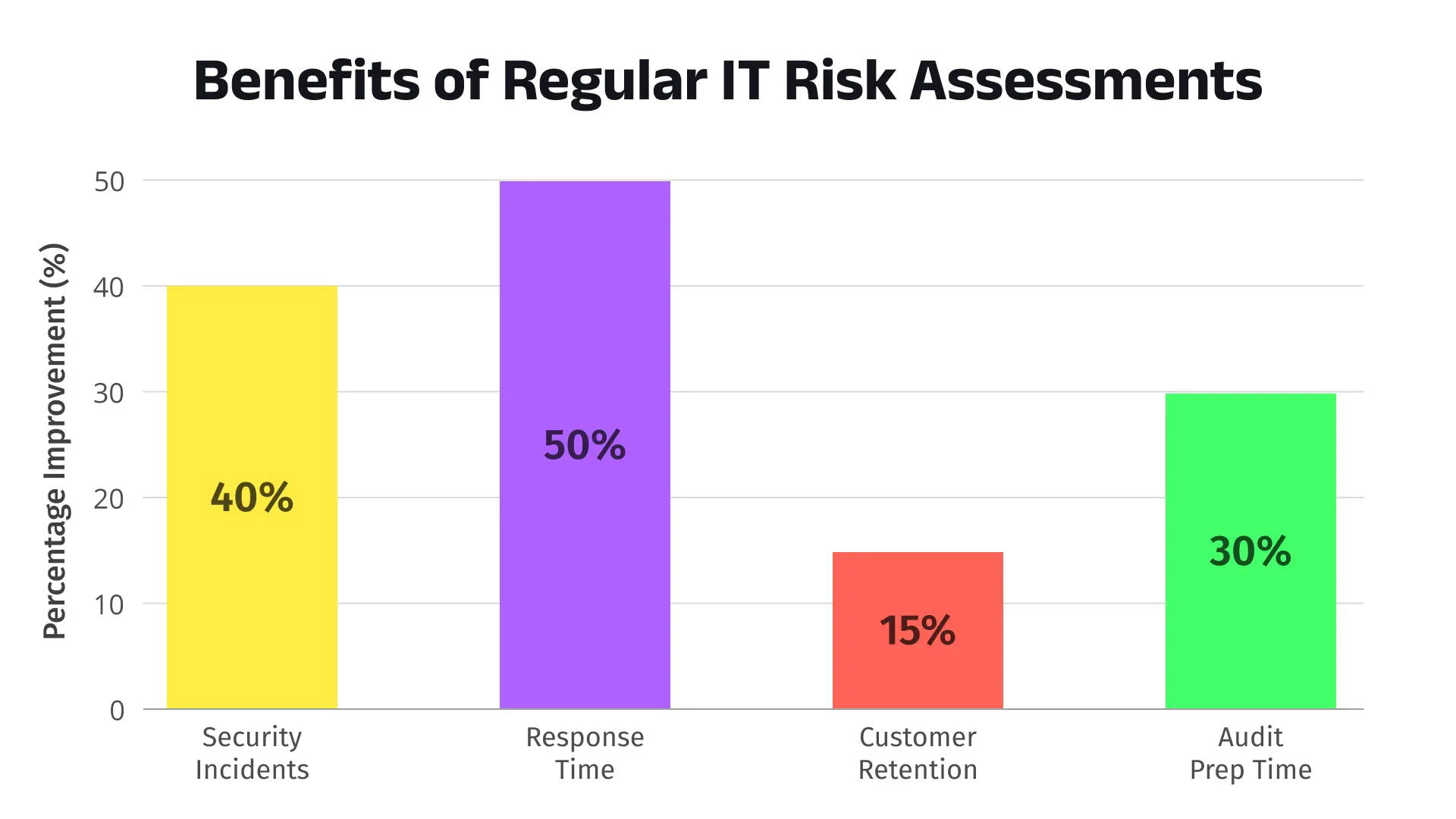
We recently worked with a fast-growing e-commerce brand that hadn’t performed a thorough risk assessment in over a year. Our team uncovered a critical vulnerability in their payment gateway’s API. Left unchecked, it could’ve opened the door to credential stuffing attacks. By implementing a Web Application Firewall (WAF), multi-factor authentication (MFA), and scheduled penetration testing, the client reduced breach exposure by 40% within six months.
Using tools like Nessus, AI-driven threat detection, and SIEM platforms, we help businesses identify and neutralize threats like malware, misconfigured cloud systems, or outdated software before attackers can exploit them. The outcome? Up to 30% fewer security incidents and significantly lower recovery costs.
2. Improved compliance with regulations
Whether it’s GDPR, HIPAA, PCI-DSS, or FISMA, failing to meet regulatory standards isn’t just risky—it’s expensive.
One of our healthcare clients approached us overwhelmed by the shifting compliance requirements. By embedding compliance audits into their risk assessment process, we helped them identify gaps in patient data protection, implement end-to-end encryption, and document their controls in a centralized risk register. Not only did this prepare them for audits, but it also reduced their risk of penalties and legal exposure.
We often recommend platforms like ServiceNow GRC and OneTrust to streamline governance. These tools help organizations maintain alignment with global security standards, such as ISO 27001, automate reporting, and provide peace of mind to auditors and stakeholders alike.
3. Optimized resource allocation
Cybersecurity budgets are tight, especially in startups and SMBs. That’s why it’s essential to know which risks to tackle first.
For example, a financial services company we partnered with faced a dilemma: invest in additional firewall layers or address a potential SQL injection vulnerability in their legacy systems. Through a risk scoring workshop, we helped them assess impact and likelihood. The SQL injection risk scored an 8/10 and took priority, averting what could’ve been a catastrophic data breach.
Using AI-enhanced risk matrices and tools like RiskLens, we enable organizations to visualize their risk landscape and allocate resources where they matter most. This kind of prioritization can reduce unnecessary spending by up to 25%.
4. Increased business continuity
Risk isn’t always a hacker in a hoodie. It’s also a flood, a power outage, or a hardware failure at your primary data center.
In one case, a global logistics company we support conducted a risk assessment that revealed their data center was in a flood-prone zone. Within three months, they had geo-redundant backups, a cloud failover plan, and tested disaster recovery protocols. What could have been a week-long outage became a two-hour hiccup.
With business impact analysis (BIA) tools and tailored continuity planning frameworks, we help clients prepare for the unexpected, so when a disruption hits, operations keep humming.
5. Proactive threat detection and response
2025 isn’t the year to wait for breaches—you need to see them coming.
After helping a client launch a new cloud-native app, our continuous risk monitoring flagged an exposed API that could’ve been exploited by a zero-day attack. Within hours, our engineers had closed the vulnerability and updated detection rules in their CrowdStrike environment.
With integrations like Splunk, AI-based anomaly detection, and real-time threat intelligence feeds, we enable businesses to reduce detection and response times by up to 50%—a critical advantage in the fight against ransomware, phishing, and advanced persistent threats.
6. Enhanced stakeholder trust and reputation
Cybersecurity is no longer just a technical issue—it’s a business reputation issue.
After several high-profile retail breaches in early 2025, one of our clients—an online marketplace—took proactive steps. By conducting a public-facing risk assessment and transparently sharing their improvements (like passwordless login and device-level security checks), they increased customer retention by 15% in one quarter.
Risk assessments, when well-communicated, show customers, partners, and regulators that you take their data seriously. Using risk registers, automated control logs, and accessible executive reports, we help clients build trust that goes beyond marketing.
7. Support for strategic decision-making
Risk insights aren’t just for IT—they’re boardroom material.
A tech startup we advised used their risk assessment outcomes to justify investing in a zero-trust architecture. With our help, they mapped out risks at the organizational, operational, and technical levels. Leadership saw the value instantly, both for security and investor confidence.
Whether it’s upgrading to AI-based EDR systems or launching a new SaaS platform in a highly regulated market, strategic decisions require clear risk visibility. We build dashboards and integrations that translate assessments into action, so cybersecurity isn’t just reactive, it’s a driver of innovation.
Challenges and best practices for IT risk assessments
At Timspark, we’ve worked with organizations of all sizes—startups, fintechs, healthcare providers, and public agencies—helping them identify and manage cybersecurity risks in environments that grow more complex each year. From ransomware to AI-driven threats, 2025’s landscape is evolving faster than many businesses can adapt.
But one truth remains: effective IT risk assessments are the foundation of strong security. That doesn’t mean they’re easy. Resource limitations, internal pushback, and technological sprawl often hinder progress. In this section, our experts share real-world challenges we’ve seen across industries—and practical strategies we’ve developed to overcome them.
Challenge | Quick Example | Actionable Best Practice |
Resource limits | 3-person e-commerce IT team | Focus on crown-jewel systems, run automated scans (e.g., Nessus), channel budget to high-impact fixes |
Ever-evolving threats | Supplier ransomware almost spread via shared creds | Add always-on monitoring + threat-intel feeds (CrowdStrike); refresh risk register quarterly |
Low exec buy-in | GDPR warning finally got leadership’s attention | Translate risk into €/$, downtime, compliance fines; show ROI in an exec dashboard |
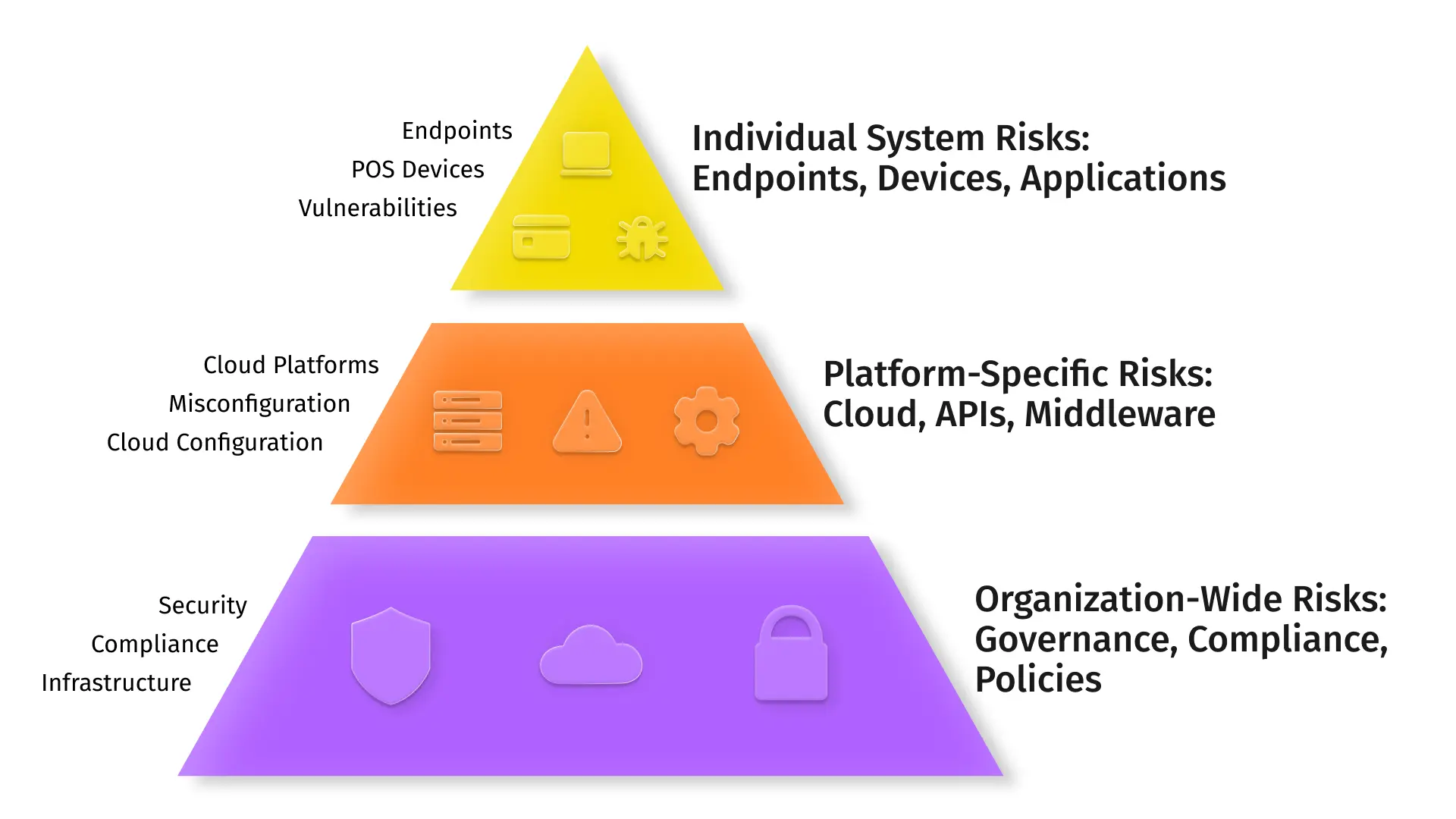
Complex, sprawling stack | Retail chain’s cloud + IoT + POS mix caused “analysis paralysis” | Tier assessments (org ? platform ? system) so teams tackle one layer at a time |
Scattered / missing docs | Prior reports buried in inboxes | Keep a single risk register with owner, impact, status—then move it into a GRC tool when ready |
Stale assessments | Vendor’s API update created new gaps overnight | Continuous scanning (Tenable.io) plus an annual full review to catch big shifts |
We recommend updating risk assessments at least annually, or after major changes. Technology moves fast, but with the right triggers and monitoring in place, your risk program can keep pace.
Tools and technologies for IT risk assessments
By 2025, risk assessments aren’t just a checklist exercise—they’re an ongoing process supported by technology that adapts as quickly as threats do. At Timspark, we help clients implement toolsets that turn assessments into living, dynamic practices. Here are the seven types of tools we rely on most.
Vulnerability scanners
These are your frontline scouts. Tools like Nessus, Qualys, or OpenVAS scan your systems for unpatched software, misconfigurations, and known weaknesses.
In one instance, we assisted a retail client in identifying a misconfigured cloud database that exposed customer records. Within hours of scanning, we applied patches and updated firewall rules.
Key Features: Automated scanning, CVE mapping, and remediation suggestions.
Integration Tip: Feed scanner data into your SIEM for live alerting.
Impact: Clients typically see a 60% reduction in vulnerability detection time.
Threat intelligence platforms
If scanners are scouts, threat intelligence platforms are radar towers. Tools like CrowdStrike Falcon or Recorded Future provide real-time alerts on emerging attacks.
One financial client detected a supply chain attack against a partner and tightened access controls in a timely manner.
Key Features: Threat scoring, dark web monitoring, IOC tracking.
Integration Tip: Connect to firewalls and SIEMs for auto-response.
Impact: Threat detection times cut in half.
Security information and event management (SIEM) systems
SIEM tools, such as Splunk, Microsoft Sentinel, and QRadar, consolidate all your logs and identify potential issues.
In healthcare, we used Sentinel to detect unusual access patterns in a patient portal, leading to a policy shift toward mandatory MFA.
Key Features: Real-time alerts, log correlation, anomaly detection.
Integration Tip: Combine with EDR tools for full visibility.
Impact: 50% faster response, 35% better detection accuracy.
Governance, risk, and compliance (GRC) platforms
Platforms like ServiceNow, RSA Archer, or OneTrust help centralize all your risk-related data and keep stakeholders informed.
For a government agency, we built a dynamic dashboard that tracked phishing threats and mapped mitigation steps.
Key Features: Risk registers, workflows, compliance dashboards.
Integration Tip: Sync with vulnerability and incident management systems.
Impact: 40% faster documentation, 30% less prep time during audits.
Cloud security tools
Cloud environments require specialized oversight. Tools like AWS Config, Microsoft Defender for Cloud, and Prisma Cloud continuously analyze your cloud settings.
One client discovered an exposed S3 bucket using Prisma before attackers did.
Key Features: Misconfiguration alerts, compliance reporting, and automated remediation.
Integration Tip: Plug into CI/CD pipelines for proactive controls.
Impact: 45% lower breach risk in cloud environments.
Penetration testing tools
To know your defenses, test them. Tools like Metasploit, Burp Suite, or Kali Linux simulate attacks and identify vulnerabilities.
An e-commerce client used Burp Suite to uncover SQL injection vulnerabilities and immediately implemented a WAF.
Key Features: Exploit simulations, session testing, vulnerability reports.
Integration Tip: Use in tandem with scanners for validation.
Impact: 30% lower likelihood of successful breaches.
Risk scoring and visualization tools
Sometimes, the biggest challenge is getting decision-makers to see the risk. Tools like RiskLens, Power BI, and Tableau help executives visualize complex data.
A manufacturing client used RiskLens to quantify the business impact of a DDoS attack, justifying a major firewall upgrade.
Key Features: Cyber risk quantification, heat maps, and dashboards.
Integration Tip: Sync with GRC or SIEM for real-time updates.
Impact: 25% better prioritization, 20% more executive buy-in.
Case in point: dbt-based logic replaced manual processes for consistent and scalable risk evaluation
Even with robust tools and frameworks, risk assessments can fall short without the right strategic execution. In one engagement, we supported a global pharmaceutical leader needed real-time insight into vendor and material risks, but siloed SAP data, spreadsheets, and ad-hoc scoring bogged decisions down.
The Challenge:
Fragmented sources and manual risk assignments produced delays and inconsistencies, threatening supply-chain continuity.
Our Approach:
We unified all feeds in a Snowflake Data Vault, automated risk logic with dbt, and exposed the results through interactive Tableau dashboards. CI/CD tests in GitLab kept data-integration accuracy at 100 %.
The Result:
Procurement teams now see ranked vendor/material risks in seconds, cutting manual effort by 40 % and enabling faster, data-driven decisions across the supply chain.
Conclusion: make risk assessments work for you
IT risk assessments aren’t just about compliance checklists or technical audits—they’re about building a resilient, responsive security posture that evolves with your business. Whether you’re dealing with resource constraints, complex environments, or shifting threat landscapes, the key is to tailor your approach: prioritize what matters, automate where possible, and turn insights into action.
At Timspark, we believe that risk assessments should empower, not overwhelm. From startups to public-sector agencies, we help teams simplify complexity, gain visibility, and make security a shared responsibility.
Ready to make your IT risk assessments more effective?
Let’s discuss how we can support your goals—whether you’re starting from scratch or scaling your existing program.
Contact us today to schedule a free consultation with our cybersecurity experts!
Frequently Asked Questions (FAQ) on IT Risk Assessments
Here is a compilation of the most commonly posed questions along with their answers.
What is an IT risk assessment?
An IT risk assessment is a systematic process that identifies, evaluates, and prioritizes risks to your information systems, enabling the development of effective mitigation strategies. Our company emphasizes that it involves cataloging threats, such as phishing or malware, and vulnerabilities, including unpatched software or weak encryption, and then implementing controls like multi-factor authentication (MFA).
For example, Universal Health Services assessed ransomware risks to its Electronic Health Record (EHR) system to ensure HIPAA compliance, as detailed in our case studies. Assessments safeguard data, systems, and operations against the evolving cyber threats of 2025.
Learn More: Explore our Portfolio for practical examples and insights.
Who is responsible for conducting IT risk assessments?
The experts recommend that IT security teams, compliance officers, and business leaders collaborate to conduct IT risk assessments. IT teams identify technical risks, such as API vulnerabilities, while compliance officers ensure alignment with regulations like GDPR or FISMA, and executives prioritize strategic risks. For instance, Capital One’s assessment involved IT and vendor management teams to address supply chain risks, as shown in our case studies. This cross-functional approach ensures comprehensive risk coverage across your organization.
How often should you conduct an IT risk assessment?
We advise conducting IT risk assessments at least annually or after significant changes, such as system upgrades, new vendor integrations, or cyber incidents. For example, the Florida Emergency Communications Center (ECC) performed an assessment after a 2023 malware attack to secure its dispatch system, as noted in our case studies. Regular assessments address risks such as zero-day exploits and cloud misconfigurations, reducing the likelihood of breaches by up to 50%. Tools like Splunk enable continuous monitoring to complement periodic reviews.
What is a risk register, and why is it important?
A risk register is a critical document that tracks identified risks, their likelihood, impact, current controls, and mitigation plans, according to the Timspark Experts. For example, Universal Health Services utilized a risk register to document ransomware risks, detailing controls such as endpoint detection and response (EDR), thereby ensuring transparency for HIPAA audits. Risk registers support compliance with regulations like PCI-DSS and streamline remediation, improving audit readiness by 30% when managed with tools like ServiceNow.
Why are IT risk assessments critical for organizations?
IT risk assessments are essential for reducing breach risks, ensuring compliance, optimizing resources, and building stakeholder trust, as the Timspark Team has seen in cases like Capital One, which saved $1.8 million by mitigating supply chain risks. Assessments quantify impacts, such as $5 million in potential downtime losses, enabling prioritized controls like firewalls or MFA. In 2025, with AI-driven threats and cloud adoption surging, assessments cut incident response times by up to 60% and boost customer retention by 15%, ensuring resilience.
What tools are used for IT risk assessments?
The Timspark Experts recommend tools like vulnerability scanners (e.g., Qualys), SIEM systems (e.g., Splunk), threat intelligence platforms (e.g., ThreatConnect), and GRC platforms (e.g., RSA Archer) to streamline IT risk assessments. For instance, the Florida ECC used Metasploit for penetration testing to identify malware vulnerabilities, as highlighted in our case studies. These tools detect threats, assess controls, and document findings, enhancing efficiency by 40% and supporting robust risk management.
How do IT risk assessments support compliance?
IT risk assessments ensure compliance with regulations such as HIPAA, GDPR, and FISMA by identifying risks and implementing controls, leveraging the Timspark Team’s expertise. For example, Universal Health Services documented ransomware mitigations in a risk register to meet HIPAA requirements, avoiding fines up to $1.5 million, as shown in our case studies. Tools like ServiceNow streamline compliance reporting, reducing audit preparation time by 30% and ensuring regulatory adherence in 2025’s stringent environment.
Learn more: See our Case Studies for compliance examples.