API Security Management: Best Practices to Secure Your APIs in 2025
April 10, 2025
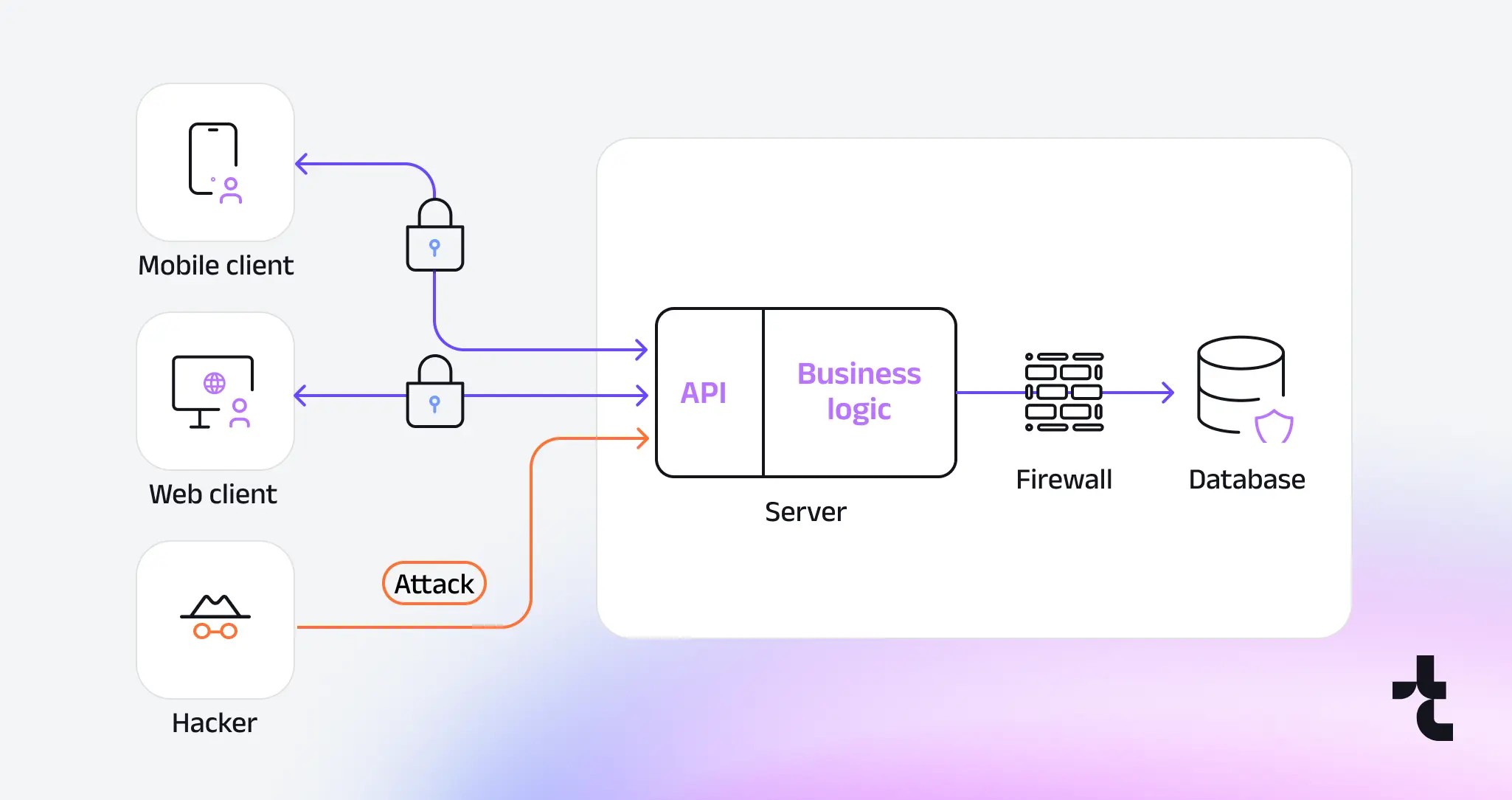
APIs are the backbone of modern applications, connecting everything from mobile apps to cloud platforms—but they’re also prime targets for attackers. In 2025, with API usage skyrocketing and threats evolving, effective API security management is non-negotiable. A single misstep, like weak authentication or an outdated endpoint, can expose sensitive data or cripple your systems.
This guide dives into the best practices to secure your APIs, blending proven strategies with forward-looking tactics tailored for today’s digital landscape. From implementing multi-factor authentication (MFA) to securing API versioning and enabling real-time monitoring, we’ll cover actionable steps to keep your APIs safe.
Whether you’re a developer, IT manager, or security pro, you’ll find practical tips to strengthen your defenses and stay ahead of emerging risks. Let’s explore how to manage API security like a pro in 2025.
Why API security management matters
APIs are everywhere in 2025 – powering seamless integrations across apps, cloud services, and IoT devices – but their ubiquity makes them a magnet for cyberattacks.
Poor API security management can lead to devastating breaches, exposing sensitive data like customer records or financial details.
For instance, recent reports indicate that API-related incidents accounted for a significant share of data breaches in 2024, often due to simple oversights such as misconfigured endpoints or weak authentication.
The OWASP API Security Top 10 underscores common risks, such as broken authentication and excessive data exposure, which can cripple businesses through fines, downtime, or reputational damage.
Top API Security Management Best Practices
Ready to lock down your APIs? This section dives into the core practices that define API security management in 2025.
We’re talking multi-factor authentication, versioning, vulnerability scanning, real-time monitoring, and secure coding – each a critical piece of the puzzle.
These aren’t just buzzwords; they’re battle-tested steps to stop attackers cold, whether they’re after your data or your uptime. With threats evolving fast, these strategies blend practicality with forward-thinking tools and tactics. Let’s dig into how to make your APIs a fortress, not a target.
Implement Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is your first line of defense for APIs. It’s simple: even if an attacker snags a password, they’re stuck without that second factor—like a code texted to a user’s phone or a biometric scan.
Industry stats peg MFA as blocking up to 99% of account takeover attempts, and in 2025, with phishing and credential stuffing surging, that’s a game-changer. Tools like Okta, Auth0, or even Google Authenticator integrate easily with API gateways or identity platforms – think AWS IAM or Azure AD.
Start by rolling it out for admin APIs, where a breach hurts most, then scale to public endpoints if they handle sensitive data. The setup’s straightforward: generate a token, tie it to a user, and enforce it at login. Yes, it adds a step, but the trade-off is ironclad protection.
Keep it user-friendly—nobody likes a clunky verification dance—and test it under load to avoid bottlenecks. Done right, MFA turns a weak link into a steel gate.
Secure API Versioning
Versioning isn’t just about updates—it’s about keeping your APIs secure by killing off old, risky endpoints.
Picture this: a v1 API from 2023 with a known flaw sits forgotten while attackers poke at it. That’s a disaster waiting to happen. Use semantic versioning—like v1.0, v1.1, v2.0—in your URLs (e.g., api.example.com/v2/resource) to track changes cleanly.
Set a deprecation schedule—say, 6-12 months after a new version drops—and stick to it. Announce it loudly and clearly via HTTP headers (e.g., Deprecation: 2025-12-31) or a changelog on your dev portal. Tools like Postman or Swagger (now part of SmartBear) can test transitions, ensuring clients don’t break when v1 fades out.
In 2025, attackers love scanning for legacy endpoints—don’t give them the chance. Deprecate aggressively, document religiously, and keep only what’s secure and supported. It’s a quiet win: users barely notice, but your attack surface shrinks fast.
Use Automated Vulnerability Scanning
You can’t secure what you don’t see, and that’s where automated vulnerability scanning shines. Tools like OWASP ZAP, Snyk, or Burp Suite sweep your APIs for holes—think misconfigured headers, SQL injection risks, or outdated dependencies. Run them weekly, or trigger scans after every code push, because in 2025, threats don’t wait.
OWASP ZAP is free and open-source—start there, point it at your API, and watch it flag issues like exposed tokens. Snyk digs deeper into code libraries, catching that old version of Jackson you forgot to patch.
Pair this with occasional pen testing for the big guns, but automation’s your daily bread—it’s fast, consistent, and doesn’t miss the small stuff. Results come with fix suggestions: update a package, tweak a setting, done. It’s not sexy, but it’s a lifesaver—especially when a zero-day drops and you’re already patched.
Enable Real-Time Monitoring
Real-time monitoring is your API’s watchdog. Imagine a 3 a.m. flood of requests—normal traffic, or a brute force attack?
Tools like Splunk, Datadog, or even AWS CloudWatch catch it live, tracking call rates, error codes, and odd patterns. In 2025, AI-driven attacks hit fast—batch logs from yesterday won’t cut it. Set up alerts: 50 failed logins in a minute? Notify the team. A 500-error spike? Check it now.
Integrate with your API gateway—say, Kong or Apigee—for end-to-end visibility. Test it with fake traffic (e.g., a script hitting your endpoint) to tune thresholds—too tight, and you’re swamped with false positives; too loose, and you miss the real deal. It’s not just detection; it’s speed—catch a breach early, and you save millions. Think of it as a live dashboard that never sleeps.
Educate Teams on Secure Coding
Secure coding is where API security starts—get it wrong, and no tool can save you. Train your devs to sanitize inputs: in Python, re.sub(r'[<>\;]’, ”, input) strips out injection bait like <script>. In Java, use prepared statements (PreparedStatement stmt = conn.prepareStatement(query)) to dodge SQL attacks.
Hardcoded keys? Never—use environment variables instead. Tools like SonarQube or Checkmarx scan code as you write, flagging sloppy habits. In 2025, human error’s still king—think exposed API keys on GitHub or unvalidated JSON.
Run monthly workshops: walk through a real injection exploit, then fix it live. Test edge cases—empty inputs, giant payloads—to harden your APIs. It’s not just rules; it’s culture. A team that codes securely hands attackers nothing to work with.
Summary Table: How These Practices Address Key Vulnerabilities
OWASP ID | API vulnerability (briefly) | How to prevent |
API1:2023 | Unauthorized access to user data | - Implement robust access controls based on user policies and hierarchy, along with authentication mechanisms. |
API2:2023 | Weak authentication | - Implement standardized practices for authentication, token generation, and password storage, incorporating robust security measures (re-authentication for sensitive operations and multi-factor authentication). |
API3:2023 | Unauthorized changes to data | - Ensure only authorized users access object properties via API endpoints, avoid generic methods like to_json() or to_string(). |
API4:2023 | Unlimited resource use | - Implement rate limiting and throttling to prevent denial-of-service attacks and resource exhaustion. |
API5:2023 | Unauthorized function use | - Implement consistent authorization across your application. |
API6:2023 | Unprotected sensitive processes | - Identify business vulnerabilities. |
API7:2023 | Server manipulation | - Validate and sanitize input data to prevent attackers from manipulating server-side requests via SQL injections, XSS, and command injection. |
API8:2023 | Poor security settings | Regularly audit and update security configurations to ensure that they align with industry best practices and security standards. |
API9:2023 | Outdated API management | - Implement robust API lifecycle management practices. |
API10:2023 | Trusting unverified data | - Validate and sanitize data from external APIs to prevent injection attacks and other security vulnerabilities. |
API Security Management Checklist
Securing your APIs is more than ticking boxes—it’s about building a strong foundation, protecting data in transit, and making sure your systems and team stay ahead of threats. A great entry point is ISO/IEC 27001, which provides a framework for an Information Security Management System, covering policies, controls, monitoring, and incident response. Here’s a concise checklist to keep your APIs safe:
- Start with authentication and access control. Enable multi-factor authentication (MFA) for admin and sensitive endpoints, use OAuth 2.0 and OpenID Connect for reliable access, and enforce strict role-based permissions so users only get what they actually need.
- Keep your APIs current with semantic versioning (v1.0.0, v2.0.0), deprecate old versions on a clear schedule, and maintain a public changelog to make client migrations seamless.
- Encrypt all traffic using TLS, preferring version 1.3 for modern security and performance. If legacy systems force your hand, TLS 1.2 is acceptable, but treat it as temporary. Regularly check certificates to avoid downtime or security gaps.
- Limit data exposure by validating all API responses. Return only what’s necessary, avoid exposing personally identifiable information (PII), and handle JSON Web Tokens (JWT) carefully—these compact, signed tokens securely transmit user identity between client and server. Use them to authenticate requests and encrypt any sensitive payloads.
- Use security headers like CSP and X-Content-Type-Options, set Cross-Origin Resource Sharing (CORS) rules for trusted origins, and implement sensible rate limits to protect against brute-force attacks, credential stuffing, and denial-of-service attempts. For example, you might limit each user to 100 requests per minute, or throttle login attempts to 5 per 10 minutes.
- Monitor your APIs in real time. Use tools like Splunk, Datadog, or CloudWatch to track anomalies, traffic spikes, and failed logins. Make sure your logs never store passwords, tokens, or other sensitive information.
- Scan and test for vulnerabilities. Combine automated scans with tools like OWASP ZAP, Snyk, or Burp Suite, and complement them with periodic penetration tests to catch anything your automated tools might miss.
- Finally, embed security in your code. Train developers on validation, sanitization, and avoiding hardcoded secrets. Leverage SonarQube or Checkmarx and hold regular workshops to make security part of your team’s culture.
Follow this checklist, and your APIs won’t just survive—they’ll thrive in 2026.
Tools and Technologies for API Security Management
Securing your APIs isn’t just about knowing what to do—it’s about having the right tools to get it done. In 2025, the API security landscape is packed with technologies that make best practices like MFA, monitoring, and scanning easier to implement. Here’s a rundown of the top tools and technologies to strengthen your API security management, each paired with the practices they support.
For multi-factor authentication (MFA), Okta and Auth0 are go-to solutions. Okta integrates seamlessly with API gateways like AWS API Gateway, letting you enforce MFA across all endpoints with minimal setup—think single sign-on (SSO) with a second factor like a push notification. Auth0 offers similar flexibility, plus adaptive MFA that adjusts based on risk (e.g., requiring a code for unusual logins). Both handle the heavy lifting, so you can focus on scaling securely.
When it comes to secure API versioning, Postman and Swagger (now part of SmartBear) are your allies. Postman lets you test version transitions—say, moving from v1 to v2—by simulating client requests and checking for breaks. Swagger’s OpenAPI specs help document versions clearly, ensuring your changelog is developer-friendly and reducing migration headaches.
For automated vulnerability scanning, OWASP ZAP and Snyk lead the pack. OWASP ZAP is free, open-source, and perfect for beginners—just point it at your API, and it’ll flag issues like exposed headers or injection risks. Snyk goes deeper, scanning your code and dependencies for vulnerabilities (e.g., an outdated library with a known CVE). It integrates with CI/CD pipelines, so scans run automatically on every commit.
Real-time monitoring gets a boost from Splunk and Datadog. Splunk’s robust logging captures every API call, letting you set alerts for anomalies—like a sudden 500-error spike. Datadog offers similar visibility with a slick dashboard, plus machine learning to predict threats (e.g., spotting a brute force attack before it escalates). Both integrate with gateways like Kong or Apigee for end-to-end coverage.
Finally, for secure coding, SonarQube and Checkmarx help your team write cleaner code. SonarQube scans as you code, flagging issues like hardcoded keys in real-time—think of it as a linter for security. Checkmarx takes it further with static analysis, catching complex vulnerabilities like SQL injections before they hit production. Pair these with regular training, and your team’s output gets safer with every sprint.
These tools aren’t just nice-to-haves—they’re your toolkit for turning best practices into reality. Pick the ones that fit your stack, and you’ll be well on your way to bulletproof APIs in 2025.
Conclusion: Building a Secure API Future
API security isn’t a one-and-done task—it’s an ongoing commitment, especially as we navigate the complexities of 2025. With APIs powering everything from mobile apps to IoT ecosystems, the stakes have never been higher. Attackers are smarter, leveraging AI to exploit vulnerabilities faster than ever, but you’re now equipped to stay one step ahead.
By implementing multi-factor authentication, securing your API versioning, running regular vulnerability scans, enabling real-time monitoring, and embedding secure coding into your team’s DNA, you’ve built a robust defense system. These practices, backed by tools like Okta, Snyk, and Datadog, turn your APIs from potential weak points into fortified gateways.
Looking ahead, the future of API security lies in proactivity. Keep an eye on emerging threats—like AI-driven attacks or quantum computing risks—and adapt your strategies accordingly. Regularly revisit this checklist and tools to ensure your APIs evolve with the threat landscape. A secure API isn’t just about protection; it’s about enabling innovation with confidence, knowing your systems can handle whatever comes next.
Ready to take your API security to the next level? Contact us if you need expert guidance, Timspark’s team is here to help—whether it’s implementing MFA, setting up monitoring, or training your developers. Let’s build a secure API future together, starting today.
Need API security services ?
References
- T-Mobile hacked to steal data of 37 million accounts in API data breach. Bleeping Computer LLC, 2023.
- Hackers exposed 2.6 million Duolingo users, more available for scraping. Cybernews, 2023.
- OWASP Top 10 API Security Risks – 2023. OWASP, 2023.
- ISO/IEC 27001:2022 Information security, cybersecurity and privacy protection — Information security management systems — Requirements. ISO, 2022.
- SAST, DAST, IAST, and RASP: Pros, cons and how to choose. Open Text Corporation, 2024.
Related Articles
A Comprehensive Guide to Software Development in Healthcare
From understanding certification requirements to exploring types of healthcare software, it’s an essential read for anyone interested in IT’s role in healthcare.
Driven to Succeed: Exploring the Software Development Methods
Dive into our comprehensive guide on how to choose the right software development approach that can transform your project, ensuring timely delivery and top-notch quality.
Custom AI Solutions vs. Ready-to-use AI: What to Choose for Your Business?
Delve in our comprehensive overview to weight between tailored and off-the-shelf AI solutions and decide which best fits the needs of your business.